From ancient Greek navigators to predictive security: how feedback loops and self-adaptation are transforming government compliance.
I. Continuous Risk Management: From Maps to Models
Picture me in December 2008, a 20-year-old private in the 82nd Airborne walking through a Baghdad market. I had just arrived in Iraq a week prior, and it was my first time out on the city streets. As I turned a corner, two men stared me down with the kind of hard look that only a life of adversity produces. They were unarmed, but when they saw me tense up, they laughed. I had combat armor, an automatic rifle, and a squad to back me up, but none of those defenses mattered against a psychological attack vector. That experience taught me something fundamental about security: you can't control everything, so you better get good at adapting quickly.
Years later, after trading my rifle for a GSA PIV card, I found myself working on FedRAMP 20x. FedRAMP 20x is a government initiative aimed at transforming how the world thinks about cloud security authorization. The irony wasn't lost on me. In Iraq, I learned that overly rigid defensive postures can still fail against adaptive threats, even when there is extreme resource asymmetry. In cybersecurity, we've been making the same mistake with compliance. This realization sent me searching for better models of adaptive security. The solution, it turns out, has ancient roots.
As ancient Greek mariners gazed out over the wine-dark waters of the Aegean Sea, they consulted bronze plates scratched with calculations to set their course. Maps were among humanity's first tools for shaping the future, improving the odds of a successful voyage.
The Greeks called these skilled navigators kybernetes (κυβερνήτης): helmsperson, pilot, rudder. Their success stemmed from something revolutionary: they had discovered how to convert lived experience into models that could guide future decisions. When they encountered a dangerous passage, they encoded it into their bronze geospatial framework. The better they became at sailing, the more data they collected, creating a self-reinforcing feedback loop that incrementally improved their navigational capabilities.
But ancient mapmaking had severe limitations. The feedback loop took months to complete, and crucial information was often lost. Reality changes constantly. Erosion transforms coastlines. Storms make normally safe waters deadly. Political boundaries shift. Even the best models drift towards inaccuracy and eventual obsolescence. The ancients were constantly humbled by unpredictable forces that swept their best-laid plans aside with complete disregard.
Over two millennia, humans have dramatically improved both our ability to create realistic models and the speed at which we can update them. The Renaissance and Enlightenment revealed natural laws that could be understood and harnessed. Probability theory allowed us to quantify uncertainty. Computers enabled us to store and analyze vast amounts of information. Today, virtually every field uses modeling to simulate reality and predict outcomes.
Enter modern cybernetics. Cybernetics was developed by Norbert Wiener in 1948 as the study of control and communication in systems. Cybernetic systems are defined by two characteristics: continuous feedback loops and self-adaptation. These principles have influenced how we think about complex systems and contributed to concepts used in modern computing, from social media to artificial intelligence. Where ancient navigators updated their bronze plates seasonally, today's Global Positioning System updates routing decisions in real-time. Sensors deployed across the globe monitor traffic, weather, road closures, and accidents, comparing them to our current location and planned route. The system continuously controls the error between us and our destination by dynamically adjusting our path. The GPS receiver continuously optimizes toward its point of convergence: our destination.
Figure 1: Human Magicians (From The Ouroboros to Continuous Integration/Continuous Deployment)
Cybernetic systems use feedback loops for dynamic adaptation rather than static planning. Ancient maps told you where things were; modern cybernetic systems tell you how to get where you want to go, even as the situation continually changes. The difference isn't just technological, it's philosophical. Cybernetic systems accept that perfect information is impossible and instead aim for continuous course correction based on the best available data.
Traditional security frameworks, like ancient maps, provide static representations of risk at a specific point in time. They don't help us navigate the constantly shifting landscape of emerging threats, evolving technology, and changing business requirements.
FedRAMP 20x represents the cybernetic evolution of compliance. Instead of annual authorization cycles, FedRAMP 20x envisions continuous authorization based on real-time risk information. This approach requires extensive automation, but it doesn't remove humans from the loop. Rather, it positions them where they add the most value. Humans excel at contextual decision-making, ethical reasoning, and strategic planning. Machines excel at data processing, pattern recognition, and consistent execution. FedRAMP 20x leverages the strengths of both while compensating for the limitations of each. Instead of providing Authorizing Officials paper maps and saying "good luck," it positions them as informed navigators of cyberspace, capable of making continuous risk decisions based on current intelligence.
The essential insight driving this transformation is that FedRAMP 20x focuses on convergence points over time rather than perfect control. The goal is not to eliminate all risk (an impossible task) but rather to continuously move toward acceptable and ever-improving risk levels while maintaining operational effectiveness.
For Authorizing Officials, this represents a paradigm shift. They move from performing administrative oversight to engaging in strategic leadership. Continuous assurance empowers AOs to focus on defining risk tolerance and making informed decisions about acceptable trade-offs between security and operational requirements based on current threat intelligence, business requirements, and available mitigations. They become skilled navigators guiding our systems to a trustworthy port of call, who can adapt their route based on current conditions.
This shift from periodic control to continuous navigation represents the foundational principle underlying everything in FedRAMP 20x.
II. Standards as Guardrails: Defining Desired Security Outcomes
Traditional FedRAMP compliance relies on lagging indicators that measure what already happened. These metrics are easy to verify (like counting high-severity CVEs), but only tell us about past performance, creating a reactive management cycle.
In contrast, FedRAMP 20x prioritizes leading indicators, or Key Security Indicators (KSIs), that predict what's likely to happen. By identifying trends and patterns before problems manifest, KSIs enable proactive course corrections.
Leading indicators are used in a wide variety of disciplines to predict future outcomes. For example, consider that modern AI systems use similar principles. Instead of trying to capture every possible variable in the universe to determine causality, they identify essential attributes that correlate with desired outcomes. Just as physics discards non-essential attributes of a falling object (like color) to focus on essential ones (like mass), transformer-based AI models use correlation patterns between essential attributes to predict future outcomes with remarkable accuracy.
Of course, there's still a distinct possibility that things could go sideways. Cybernetic systems are capable of diverging in unpredictable ways. When feedback loops optimize for specific metrics, they drift toward unexpected outcomes that technically meet objectives while undermining actual intent. A GPS system that optimizes the fastest route by directing us to drive off a cliff is no good. Similarly, an automated vulnerability management system might meet an objective to remediate findings rapidly by suppressing legitimate findings rather than flagging them. This is why the standards such as the Vulnerability Disclosure and Reporting (VDR) and the Significant Change Notification (SCN) are just as critical as the KSIs themselves. They prevent the system from going off the rails.
But the FedRAMP 20x standards alone cannot enforce secure outcomes. The FedRAMP 20x standards must be enforced by cloud service providers via compliance automation that relies on policy as code. Building a policy engine using tools like Open Policy Agent (OPA), Steampipe, and Kyverno is essential. My work during the FedRAMP Agile Delivery Pilot, which helped inform FedRAMP 20x, identified four core types of automated policies that CSPs can combine to create a flexible and reliable compliance automation engine that maintains human oversight:
Immutable policies encode non-negotiable security requirements. Think of them as constitutional rights made executable. When violated, the system blocks the action immediately. These represent the absolute boundaries that cannot be crossed regardless of business justification. For example, a policy that prevents the storage of unencrypted sensitive data in Internet-reachable databases.
Threshold policies provide flexibility for context-dependent boundaries. Instead of absolute rules, they define acceptable ranges and trigger actions when metrics drift outside those ranges. For example, a policy that allows normal user access patterns but triggers additional authentication requirements when unusual access patterns are detected.
Intelligent decision policies categorize actions by applying logic, historical precedent, or simulated modeling, then decide what to do based on that categorization. These policies can learn from past decisions and improve their accuracy over time. For example, a policy that automatically categorizes vulnerabilities based on exploitability, business impact, and available mitigations, then routes them to appropriate remediation workflows.
Escalation policies identify and prioritize choices that require human discernment. The system gathers relevant context, presents options, and executes based on human decisions. These policies ensure that complex or unprecedented situations receive appropriate attention while preventing routine decisions from overwhelming human decision-makers.
These four policy types work together to implement the FedRAMP 20x standards like the VDR and SCN. The cloud service provider maintained policy engines provide the automation that makes compliance frameworks workable at scale, while the FedRAMP 20x standards prevent optimization drift that could undermine security intent.
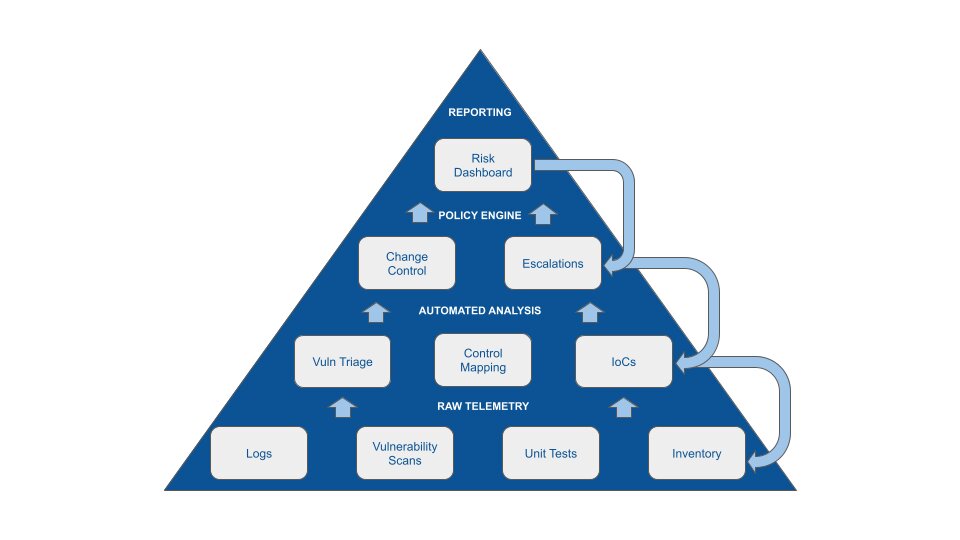
Figure 2: Automated Assurance From Data to Decision
Real World Example: Vulnerability Management Workflow
A real-world example illustrates how the FedRAMP 20x KSIs and related standards combined with policy engine enforcement simultaneously implements and demonstrates overall risk posture.
Consider a vulnerability management workflow deployed in a cloud environment. Today, due to the static "30, 90, 180" day remediation windows per severity, teams often spend enormous amounts of time addressing non-exploitable vulnerabilities while waiting to fix findings that are known to be actively exploited.
The cybernetic approach focuses instead on leveraging a policy engine and automated workflows to triage findings appropriately for prioritized remediation based on actual risk. When a scanner identifies a new vulnerability in a critical application component, the workflow gathers all the relevant contextual information about the finding, asking, "is it publicly reachable? Is it likely exploitable?"
From there, the workflow checks immutable policies and asks, "is this a vulnerability that must be patched immediately regardless of business impact?" If not, it applies threshold policies by asking, "what is our risk tolerance based on severity, exploitability, and exposure?" Intelligent decision policies determine appropriate remediation timelines based on similar historical cases.
Finally, if the situation involves unprecedented risk factors or requires architectural changes, escalation policies route the decision to human experts with full context about the risk trade-offs involved. The entire process can happen in seconds rather than weeks, providing timely intelligence about changing risk postures. The workflow also gets smarter over time as it learns from both successful and unsuccessful risk decisions.
III. The Convergence Engine: How FedRAMP 20x Empowers Stakeholders to Balance Different Objectives
One of the most sophisticated aspects of cybernetic systems is their ability to collaboratively manage competing objectives and stakeholder interests. In the context of FedRAMP, this becomes particularly important because government agencies and cloud service providers operate with different convergence points.
Corporations may operate very efficiently, but they ultimately optimize for profit maximization, not societal risk. Government agencies, by contrast, optimize for mission effectiveness. This dynamic has historically created inherent tension and inefficiency because it requires one stakeholder to accept undue risk by operating against its natural convergence point.
FedRAMP 20x offers the opportunity for cloud service providers to balance multiple convergence points directly into the policies that govern these interactions. Instead of trying to eliminate differences in objectives, automated policy engines allow organizations to anticipate where divergences are likely to occur and provide structured approaches for managing them. This design creates what we might call 'collaborative convergence', a state where competing systems find shared optimization paths rather than working at cross-purposes.
Take data residency requirements as a concrete example. Different countries require certain data types to remain within their borders, creating a conundrum for commercial cloud service providers who serve global customers. A rigid implementation would replicate the infrastructure in every country, exploding costs and complexity.
A cybernetic approach instead segments the architecture by classifying data according to both type and regulatory requirement, not just by customer. This enables intelligent routing where request processing happens at the edge while regulated data remains in compliant regions. Policy engines automate enforcement by verifying data location requirements before any transfer or processing operation occurs. The system continuously optimizes by monitoring both compliance status and infrastructure costs, consolidating resources wherever regulations permit. The result is that data residency requirements are met across multiple jurisdictions while maintaining efficient global operations.
The result is significant savings for the provider and their customers. The cloud service provider doesn't have to build redundant infrastructure in every market, and governments achieve their compliance objectives.
The key to collaborative convergence approaches is a policy engine that can balance multiple objectives simultaneously. This allows for both corporations and governments to plot their course together instead of fighting for control over the coordinates. Of course, this approach also requires shared investment to get off the ground - corporations must invest in tech while AOs must invest in new processes. If we are to achieve all of these benefits, agencies must be willing to focus on secure outcomes rather than prescriptive processes, and cloud service providers must be willing to prioritize sustainable revenue over immediate short-term profit optimization. This may not make sense for every business, and that is also fine.
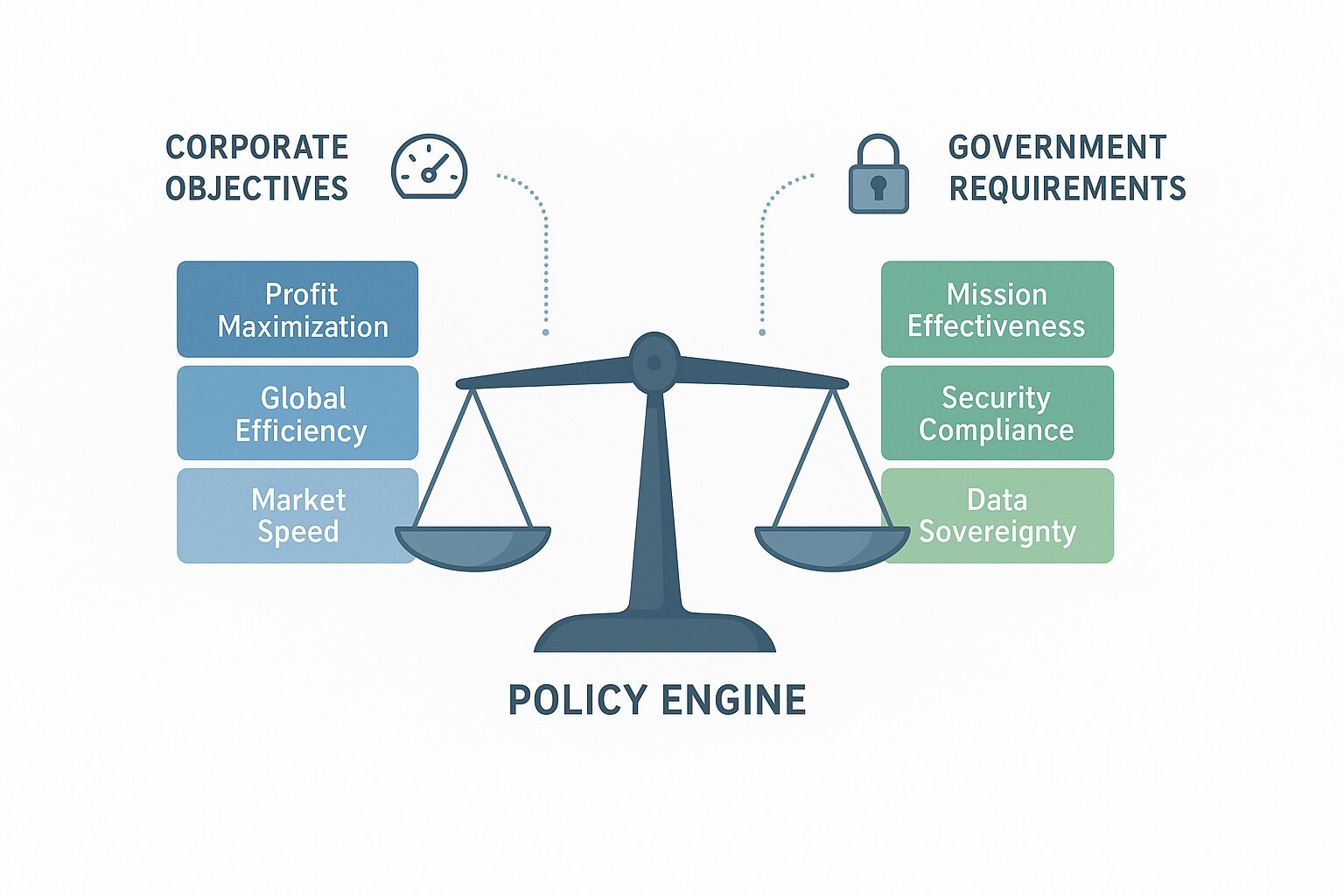
Figure 3: Collaborative Convergence for Achieving Cross-Stakeholder Objectives
The key insight is that organizations can harness the optimization capabilities of different stakeholder systems, while ensuring that collective outcomes serve broader public interests, by building collaborative convergence into policy engines. Each stakeholder achieves their own goal. AOs guide systems to trustworthy outcomes, and cloud service providers get paid for their work - a win/win!
Conclusion: The AO as a Navigator of Risk
The transformation from traditional compliance to cybernetic risk management requires skilled leadership from professionals who understand many domains: security, business, enterprise risk, and governance. Authorizing Officials occupy a unique position in this transformation because they bridge technical security requirements with broader agency missions that serve societal objectives. As navigators of risk, they play a crucial role by guiding cybernetic systems toward human flourishing rather than narrow technical and economic optimization.
Understanding the role of AOs as risk management experts is a critical distinction often overlooked in discussions of government cybersecurity. Effective cybernetic risk management requires the ability to make informed decisions about acceptable trade-offs. Perhaps more importantly, it requires professional judgment to distinguish between technical compliance and actual risk reduction.
AOs who lack enterprise risk management experience often default to either excessive risk avoidance (which paralyzes operations) or excessive risk tolerance (which creates unnecessary exposures). Both approaches undermine effective risk management because they prioritize political considerations over evidence-based decision-making.
FedRAMP 20x empowers AOs with the information and tools they need to exercise professional judgment effectively. But they still have to exercise that judgment.
At a minimum, AOs should insist on vulnerability reporting that provides meaningful insight into real-time risk rather than just historical reports about past findings. They should insist on policy engines to enforce control implementation for automated assurance.
The path to FedRAMP 20x is just as much a cultural shift as it is a technical one. Government agencies and corporations that successfully implement FedRAMP 20x often discover that the feedback loops and self-correcting mechanisms that characterize cybernetic security also provide compounding advantages across multiple functions. Why this matters beyond government becomes clear when we consider the broader implications. Organizations that master cybernetic risk management develop capabilities that enable rapid adaptation to changing conditions and effective coordination across complex stakeholder relationships. These capabilities provide competitive advantages in rapidly changing business environments and contribute to broader social stability during times of uncertainty.
The choice ahead involves deciding whether we develop cybernetic approaches that empower skilled professionals to make informed risk decisions, or whether we allow cybernetic systems to operate without appropriate human oversight and democratic accountability. AOs play a crucial role in this choice.
Ancient mariners understood that navigation demanded the wisdom to read storms, sense currents, and choose when to trust experience over calculations. Like the ancient Greek kybernetes whose success relied on both maps and discernment, today's AOs must wield sophisticated tools while maintaining the judgment to know how to use them.
Our modern navigators face incredible complexity. And the stakes couldn't be higher. Failure means public trust in government eroding under the weight of systems we no longer democratically steer.
The question of who sets the convergence points is critical. FedRAMP 20x has provided us with an exceptionally seaworthy craft. It is up to us to successfully navigate the unknown waters ahead.
Like this article? Here's another you might enjoy...